My Pc became very slow, when I opened many windows and applications.How to increase or restore my Pc speed?
when an user after using his PC several hours by opening several windows and applications.The Pc speed becomes slow so it causes hanging of PC also leads to restart of system.
this condition is due to "Memory leakage".
The used applications or programmes memory addresses are not freed though they are unloaded from the memory.
So these problem can be solved simply by a simple trick without using third Party tools like Ram Booster etc.,
follow these steps
Open a Notepad and type MYSTRING=(800000000)
save it as memory.vbe on desktop
when ever we use many applications or windows double click on the memory.vbe file and the memory leakage will be controlled
How to test a new Graphics card whether it is perfect or not?
I have bought Nvidia ,ATI Radeon graphics card . How can I test so that these are working properly or not?
there is tool for the testing of these cards .the tool named fullmark can help the user very much.
user can download this from following link
download
there is tool for the testing of these cards .the tool named fullmark can help the user very much.
user can download this from following link
download
Labels:
hardware,
troubleshooting
AntiVirus GT fake AntiVirus Tool removal !
How to remove Antivirus GT Fake AntiVirus Application ?
This type of anti virus attract many pc users who are one line regularly. This makes the user to install it and check the status. If the user installs it mistakenly oh god ! it shows the warning messages that manly a lot files are infected with virus and worms . So it tells the user to by the full programme or package quickly to remove these infected virus files.
There is a removal tool to delete this fake anbtivirus
users can download this tool from this link
download
This type of anti virus attract many pc users who are one line regularly. This makes the user to install it and check the status. If the user installs it mistakenly oh god ! it shows the warning messages that manly a lot files are infected with virus and worms . So it tells the user to by the full programme or package quickly to remove these infected virus files.
There is a removal tool to delete this fake anbtivirus
users can download this tool from this link
download
How to download Multiple files from a server with out third Party tools
If you are using IE8 and IE7 you cannot download more than two files from a server from internet without third party plugins like IDM,FlashGet.
So to download more than two files from a server in single time you have to change the registry values by Regedit
Steps :-
1. Go to Start --- Run ---regedit
2.in Registry go to Mycomputer ----HKEY_CURRENT_USER\ Software\Microsoft\Windows\Current Version\InternetSettings
3.Right Click on the Internet Settings and create a Dword MaxConnectionsPerServer give a value in decimal as 10 by change the binary value.
4.Create another Dword MaxConnectionPer1_0Server and give the Value in Decimal as 10.
thus the work is over and enjoy multiple downloads from a server without third Party Plug ins
So to download more than two files from a server in single time you have to change the registry values by Regedit
Steps :-
1. Go to Start --- Run ---regedit
2.in Registry go to Mycomputer ----HKEY_CURRENT_USER\ Software\Microsoft\Windows\Current Version\InternetSettings
3.Right Click on the Internet Settings and create a Dword MaxConnectionsPerServer give a value in decimal as 10 by change the binary value.
4.Create another Dword MaxConnectionPer1_0Server and give the Value in Decimal as 10.
thus the work is over and enjoy multiple downloads from a server without third Party Plug ins
Labels:
Registry Tricks
In OutLook Configuration which Incoming Protocol IMAP or POP ?
Most People Like IMAP configuration as incoming mail protocol In Micro Soft Out Look and other email clients because IMAP does not delete the downloaded mails from server (google or yahoo) .But POP deletes the Mails from the server.
In computing, the Post Office Protocol (POP) is an application-layer Internet standard protocol used by local e-mail clients( MicroSoft OutLook, Mozilla Thunder Bird, Evolution Client, IBM Lotus Notes) to retrieve e-mail from a remote server over a TCP/IP connection( Gmail, YahooMail etc., )
POP supports simple download-and-delete requirements for access to remote mailboxes . Although most POP clients have an option to leave mail on server after download, e-mail clients using POP generally connect, retrieve all messages, store them on the user's PC as new messages, delete them from the server, and then disconnect. Other protocols, notably IMAP, (Internet Message Access Protocol) provide more complete and complex remote access to typical mailbox operations. Many e-mail clients support POP as well as IMAP to retrieve messages; however, fewer Internet Service Providers (ISPs) support IMAP.
A POP3 server listens on well-known port 110. Encrypted communication for POP3 is either requested after protocol initiation, using the STLS command, if supported, or by POP3S, which connects to the server using Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on well-known TCP port 995 (e.g. Google Gmail).
so finally use of POP configuration in Outlook causes deletion of Mails from Gmail or yahoomail Servers .We cannot retrieve them even though we use Browsers for viewing older mails
The Internet Message Access Protocol (IMAP) is one of the two most prevalent Internet standard protocols for e-mail retrieval, the other being the Post Office Protocol (POP).[ Virtually all modern e-mail clients and mail servers support both protocols as a means of transferring e-mail messages from a server.
is an Application Layer Internet protocol that allows an e-mail client to access e-mail on a remote mail server. The current version, IMAP version 4 revision 1
MAP supports both on-line and off-line modes of operation. E-mail clients using IMAP generally leave messages on the server until the user explicitly deletes them. This and other characteristics of IMAP operation allow multiple clients to manage the same mailbox. Most e-mail clients support IMAP in addition to POP to retrieve messages; however, fewer email services support IMAP.[3] IMAP offers access to the mail store. Clients may store local copies of the messages, but these are considered to be a temporary cache.
Incoming e-mail messages are sent to an e-mail server that stores messages in the recipient's email box. The user retrieves the messages with an e-mail client that uses one of a number of e-mail retrieval protocols. Some clients and servers preferentially use vendor-specific, proprietary protocols, but most support the Internet standard protocols, SMTP for sending e-mail and POP and IMAP for retrieving e-mail, allowing interoperability with other servers and clients. For example, Microsoft's Outlook client uses a proprietary protocol to communicate with a Microsoft Exchange Server server as does IBM's Notes client when communicating with a Domino server, but all of these products also support POP, IMAP, and outgoing SMTP. Support for the Internet standard protocols allows many e-mail clients such as Pegasus Mail or Mozilla Thunderbird (see comparison of e-mail clients) to access these servers, and allows the clients to be used with other servers (see list of mail servers).
In computing, the Post Office Protocol (POP) is an application-layer Internet standard protocol used by local e-mail clients( MicroSoft OutLook, Mozilla Thunder Bird, Evolution Client, IBM Lotus Notes) to retrieve e-mail from a remote server over a TCP/IP connection( Gmail, YahooMail etc., )
POP supports simple download-and-delete requirements for access to remote mailboxes . Although most POP clients have an option to leave mail on server after download, e-mail clients using POP generally connect, retrieve all messages, store them on the user's PC as new messages, delete them from the server, and then disconnect. Other protocols, notably IMAP, (Internet Message Access Protocol) provide more complete and complex remote access to typical mailbox operations. Many e-mail clients support POP as well as IMAP to retrieve messages; however, fewer Internet Service Providers (ISPs) support IMAP.
A POP3 server listens on well-known port 110. Encrypted communication for POP3 is either requested after protocol initiation, using the STLS command, if supported, or by POP3S, which connects to the server using Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on well-known TCP port 995 (e.g. Google Gmail).
so finally use of POP configuration in Outlook causes deletion of Mails from Gmail or yahoomail Servers .We cannot retrieve them even though we use Browsers for viewing older mails
The Internet Message Access Protocol (IMAP) is one of the two most prevalent Internet standard protocols for e-mail retrieval, the other being the Post Office Protocol (POP).[ Virtually all modern e-mail clients and mail servers support both protocols as a means of transferring e-mail messages from a server.
is an Application Layer Internet protocol that allows an e-mail client to access e-mail on a remote mail server. The current version, IMAP version 4 revision 1
MAP supports both on-line and off-line modes of operation. E-mail clients using IMAP generally leave messages on the server until the user explicitly deletes them. This and other characteristics of IMAP operation allow multiple clients to manage the same mailbox. Most e-mail clients support IMAP in addition to POP to retrieve messages; however, fewer email services support IMAP.[3] IMAP offers access to the mail store. Clients may store local copies of the messages, but these are considered to be a temporary cache.
Incoming e-mail messages are sent to an e-mail server that stores messages in the recipient's email box. The user retrieves the messages with an e-mail client that uses one of a number of e-mail retrieval protocols. Some clients and servers preferentially use vendor-specific, proprietary protocols, but most support the Internet standard protocols, SMTP for sending e-mail and POP and IMAP for retrieving e-mail, allowing interoperability with other servers and clients. For example, Microsoft's Outlook client uses a proprietary protocol to communicate with a Microsoft Exchange Server server as does IBM's Notes client when communicating with a Domino server, but all of these products also support POP, IMAP, and outgoing SMTP. Support for the Internet standard protocols allows many e-mail clients such as Pegasus Mail or Mozilla Thunderbird (see comparison of e-mail clients) to access these servers, and allows the clients to be used with other servers (see list of mail servers).
Labels:
Email,
EmailCleints,
Internet,
Outlook
Internet Explorer 7,RunOnce URL (runonce.msn.com/runonce2.aspx)error!
After the installation of Internet Explorer 7, you might see a blank page instead of your Homepage, or it may keep loading the RunOnce URL (runonce.msn.com/runonce2.aspx). To fix this issue, add the following registry keys:
Hive: HKEY_CURRENT_USER
Key: \Software\Microsoft\Internet Explorer\Main
Name: RunOnceHasShown
Type: dword
Value: 1
Name: RunOnceComplete
Type: dword
Value: 1
Hive: HKEY_CURRENT_USER
Key: \Software\Microsoft\Internet Explorer\Main
Name: RunOnceHasShown
Type: dword
Value: 1
Name: RunOnceComplete
Type: dword
Value: 1
Labels:
internetexplorer,
windows
Windows Media Player Error while Connecting to internet
When Windows media Player is connected to internet for some online update or what so ever. It is not connecting to Internet and showing a error message on the screen
Windows Media Player Error C00D10B3
This can be trouble shooted by simply editing the registry.
do the following steps
1.go to Start----Run----regedit
2.go to HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Preferences
3. create a new Dword ForceOnlineby right clicking on preferences and give value 1
then from now you cannot get error message
Windows Media Player Error C00D10B3
This can be trouble shooted by simply editing the registry.
do the following steps
1.go to Start----Run----regedit
2.go to HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Preferences
3. create a new Dword ForceOnlineby right clicking on preferences and give value 1
then from now you cannot get error message
Labels:
MediaPlayer errots,
Registry Tricks,
w,
windows
Cannot Access Regedit, How to Fix It?

Cannot Access Regedit, How to Fix It?Many times when working on a computer that has been infected with a virus, trojan, or piece of spyware I find myself with my most important command, Regedit, the Windows Registry Editor being disabled. Virus creators like to disable the Registry Editor so it makes solving the problem and removing the issue difficult.Sometimes administrators in IT departments may place restrictions on using the regedit command to keep employees from changes things on company computers, but viruses and other issues may also try to disable it.Listed below you will find the different ways to enable regedit, the Registry Editor. First we'll begin with the method that appears to work the best.
Method 1 - Enabling the Registry with VBScriptDoug Knox, a Microsoft Most Valuable Professional, has created a VBScript that enables or disables the Registry Editor based on the following location in the registry. Of course, since the registry editor is disabled, you can't change it manually, so Doug wrote a Visual Basic Script to accomplish the task.HKey_Current_User\Software\Microsoft\Windows\CurrentVersion\Policies\System\Visit Doug's page and download Registry Tools VBScript to your desktop, double-click on it to run it, then reboot your computer and try to open the Registry Editor.If this fix didn't solve your problem, try method two shown below.
Method 2: Use Symantec's tool to reset shell\open\command registry keysSometimes worms and trojans will make changes to the shell\open\command registry entries as part of their infections. This will cause the virus to run each time you try to run an .exe file such as the Registry Editor. In these cases, visit Symantec's website and download the UnHookExec.inf file to your desktop. Right-click on it and choose Install. Restart your computer and then try to open the Registry Editor.
Method 3: Rename Regedit.com to Regedit.exeSome viruses and other malware will load a regedit.com file that is many times a zero byte dummy file. Because .com files have preference over .exe files when executed if you type REGEDIT in the run line, it will run the regedit.com instead of the real regedit.exe file. Delete the regedit.com file if its a zero byte file to restore access to REGEDIT. In some cases, such as the W32.Navidad worm, you'll need to rename the REGEDIT file to get it to work.
Method 4: Windows XP Professional and Group Policy EditorIf you have Windows XP Professional and access to an administrative user account, you could change the registry editor options in the Group Policy Editor.Click Start, RunType GPEDIT.MSC and Press EnterGo to the following locationUser ConfigurationAdministrative TemplatesSystemIn the Settings Window, find the option for "Prevent Access to Registry Editing Tools" and double-click on it to change.Select Disabled or Not Configured and choose OKClose the Group Policy Editor and restart your computerTry opening REGEDIT againAlthough there are a few other ways, the above ways I have used with great success in re-enabling the REGEDIT command. If you are interested in more ways to reactive the REGEDIT command, you may want to visit a site called Killian's Guide, that goes into more detail on a variety of ways to get the registry editor to work again
Labels:
Registry,
Virsus effects
How to block or unblock a website?
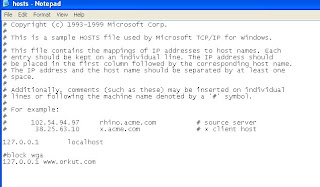
If in your office or in any organisation management blocks some websites for their security and convineince.
If we want to see these sites we have to do some modifications in the windows host file residing in system32 folder of windows
How to make the changes ?
go to start-> Run->cmd
then type the following path
notepad c:\WINDOWS\system32\drivers\etc\hosts
notepad opens websites urls are blocked with #block then remove the name and save then the website is unblocked
If we want to see these sites we have to do some modifications in the windows host file residing in system32 folder of windows
How to make the changes ?
go to start-> Run->cmd
then type the following path
notepad c:\WINDOWS\system32\drivers\etc\hosts
notepad opens websites urls are blocked with #block then remove the name and save then the website is unblocked
Labels:
networking
My Network connection Icon or option Disappered in control Pannel What should I do?
If Networking Settings options in Control Pannel Disappeared then we have a trick in registry by Editing the registry in Windows Operating System
follow the given steps
1. Go to Start --- Run ---regedit
2.go to HKEY_CURRENT_USER\Control Panel\don't load
3.go to right side frame and find the string ncpa.cpl string and delete it
follow the given steps
1. Go to Start --- Run ---regedit
2.go to HKEY_CURRENT_USER\Control Panel\don't load
3.go to right side frame and find the string ncpa.cpl string and delete it
Labels:
Registry Tricks
I cannot see Administrator in Windows Login Screen
When we boot Windows Operating System .In login or Welcome Screen Administrator account or user name is not Appearing then we must change or add a new value in registry editor
.
following steps should be done.
1. goto Start --- Run ----regedit.
2. goto key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList
3. Create a Dword name Administrator an give a value 1 by double clicking on it
.
following steps should be done.
1. goto Start --- Run ----regedit.
2. goto key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList
3. Create a Dword name Administrator an give a value 1 by double clicking on it
Labels:
Registry Tricks
Illegal System DLL Relocation error!
"Illegal System DLL Relocation"
The system DLL user32.dll was relocated in memory. The application will not run properly. The relocation occurred because the DLL C:\Windows\System32\Hhctrl.ocx occupied an address range reserved for Windows system DLLs. The vendor supplying the DLL should be contacted for a new DLL.
To resolve this problem,
download the following tool from microsoft to fix this issue
download tool
The system DLL user32.dll was relocated in memory. The application will not run properly. The relocation occurred because the DLL C:\Windows\System32\Hhctrl.ocx occupied an address range reserved for Windows system DLLs. The vendor supplying the DLL should be contacted for a new DLL.
To resolve this problem,
download the following tool from microsoft to fix this issue
download tool
Labels:
Dll errors,
windows
Only google Sites are not Opening in my Pc ?
in simple language, if u can open google like this "64.233.161.100" but not with "www.google.com" then it means that your DNS server is not working properly.
In that case, click on your Connection, the blinking icon in the right hand side. click on properties and double click on Internet protocol .
.
There'll be an entry there which says:
"OObtain Dns server automatically"
or
"Use the following DNS server address"
choose this second one and type in
"218.248.240.46"
and alternate as "218.248.255.146"
it may fix your problem.
In that case, click on your Connection, the blinking icon in the right hand side. click on properties and double click on Internet protocol

There'll be an entry there which says:
"OObtain Dns server automatically"
or
"Use the following DNS server address"
choose this second one and type in
"218.248.240.46"
and alternate as "218.248.255.146"
it may fix your problem.
Labels:
Internet
Very very inteligent dangerous worm for Computer
WormPalevo is a malicious worm that will impact your computer and your life
negatively.WormPalevo is a mass mailing type of worm that spreads and attaches itself via
emails.WormPalevo can be seen as another reason to not click on untrustworthy links.WormPalevo
is able to steal your information, invade your privacy as well as send the information which it captures to various malicious
third parties.
Worm.Palevo may go by the following names:
• WormPalevo
• Worm Palevo
WormPalevo may display some of the following symptoms:
• Files will start appearing and disappearing.
• Your computer will become increasingly slow.
• Some of your computer setting may suddenly change.
• It may feel like somebody is watching you.
• It may seem like you have a ghost on your computer.
The best advice that can be offered is for you remove WormPalevo immediately upon detection. You could make use of the
manual removal instructions but you need to be seriously warned that you run the risk of causing even further damage to
your computer if you do something incorrectly.
download tool for this worm
Can a virus hide in a PC's CMOS memory?
Can a virus hide in a PC's CMOS memory?
No.
The CMOS RAM in which PC system information is stored and backed up by batteries is accessible through the I/O ports and not directly addressable.
Further, most PCs have only 64 bytes of CMOS RAM and the use of the first 48 bytes of this is predetermined by the IBM AT specification. Several BIOS'es also use many of the "extra" bytes of CMOS to hold their own, machine-specific settings. This means that anything that a virus stores in CMOS can't be very large. A virus could use some of the "surplus" CMOS RAM to hide a small part of its body (e.g. its payload, counters, etc). Any executable code stored there, however, must first be extracted to ordinary memory in order to be executed.
This issue should not be confused with whether a virus can *modify* the contents of a PC's CMOS RAM. Of course viruses can, as this memory is not specially protected (on normal PCs), so any program that knows how to change CMOS contents can do so. Some viruses do fiddle with the contents of CMOS RAM (mostly with ill-intent) and these have often been incorrectly reported as "infecting CMOS" or "hiding in CMOS". An example is the PC boot sector virus EXE_Bug, which changes CMOS settings to indicate that no floppy drives are present
No.
The CMOS RAM in which PC system information is stored and backed up by batteries is accessible through the I/O ports and not directly addressable.
That is, in order to read its contents you have to use I/O instructions rather than standard memory addressing techniques. Therefore, anything stored in CMOS is not directly "in memory". Nothing in a normal machine loads the data from CMOS and executes it, so a virus that "hid" in CMOS RAM would still have to infect an executable object of some kind in order to load and execute whatever had been written to CMOS.
A malicious virus can of course *alter* values in the CMOS as part of its payload, but it can't spread through, or hide itself in, the CMOS. Further, most PCs have only 64 bytes of CMOS RAM and the use of the first 48 bytes of this is predetermined by the IBM AT specification. Several BIOS'es also use many of the "extra" bytes of CMOS to hold their own, machine-specific settings. This means that anything that a virus stores in CMOS can't be very large. A virus could use some of the "surplus" CMOS RAM to hide a small part of its body (e.g. its payload, counters, etc). Any executable code stored there, however, must first be extracted to ordinary memory in order to be executed.
This issue should not be confused with whether a virus can *modify* the contents of a PC's CMOS RAM. Of course viruses can, as this memory is not specially protected (on normal PCs), so any program that knows how to change CMOS contents can do so. Some viruses do fiddle with the contents of CMOS RAM (mostly with ill-intent) and these have often been incorrectly reported as "infecting CMOS" or "hiding in CMOS". An example is the PC boot sector virus EXE_Bug, which changes CMOS settings to indicate that no floppy drives are present
my pendrive cannot be formatted
method 1:
. Open Start Menu >> Run, type regedit and press Enter, this will open the registry editor.
2. Navigate to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\StorageDevicePolicies
3. Double click the key WriteProtect in the right pane and set the value to 0 in the Value Data Box and press OK button.
4. Exit Registry, restart your computer and then again re-connect your USB pen drive on your computer. That is it, done.
Reply With Quote
method 2:
1. insert the pendrive
2. dont open or format it directly
3. right click on my computer and go to manage
4. in computer management window click on disk managment option
5. right click on the removable disk (i,h....)
6. select forma
. Open Start Menu >> Run, type regedit and press Enter, this will open the registry editor.
2. Navigate to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\StorageDevicePolicies
3. Double click the key WriteProtect in the right pane and set the value to 0 in the Value Data Box and press OK button.
4. Exit Registry, restart your computer and then again re-connect your USB pen drive on your computer. That is it, done.
Reply With Quote
method 2:
1. insert the pendrive
2. dont open or format it directly
3. right click on my computer and go to manage
4. in computer management window click on disk managment option
5. right click on the removable disk (i,h....)
6. select forma
How to scan unread pen or flash drives that cannot read or showing errors?

If the pendrives or flash drives are not getting read or not opening, showing errors
use the following free tool
from the url http://mikelab.kiev.ua/PROGRAMS/ChkFlsh.zip
What is the VBS.Loveletter virus and its NewLove variant?
What is the VBS.Loveletter virus and its NewLove variant?
The ILOVEYOU virus is an email attachment written in Visual Basic and smartly disguised as a love letter. Who wouldn't want to receive a love letter afterall? The email attachment was called LOVE-LETTER-FOR-YOU.TXT.vbs and when opened wrecked havoc throughout a computer system by overwriting files or hiding them throughout the system and in the case of people using Microsoft Outlook it sent a copy of the virus to everyone in the computer's address book.
The Love Bug infects files with the following extensions: "vbs", "vbe", "js", "jse", "css", "wsh", "sct", "hta", "jpg", "jpeg", "mp3", or "mp2". Except for "mp3" and "mp2" files, the virus overwrites the whole file with its virus code and the original file is destroyed.
For "vbs" and "vbe" files the virus does not change the host filename.
For "js", "jse", "css", "wsh", "sct" or "hta" files
It changes the filename to ".vbs" (For example: MyStyleSheetFile.css is renamed as MyStyleSheetFile.vbs).
For "jpg" and "jpeg" files
It changes the filename to ".vbs" (For example: MyJPEGFile.jpg is renamed as MyJPEGFile.jpg.vbs).
For "mp3", or "mp2" files
It changes the attribute of the original audio file as the hidden system file and creates a copy of the virus self in the filename of ".vbs" (For example: with MyMP3File.mp3, the virus makes a copy of itself as a file called MyMP3File.mp3.vbs). Therefore, all "mp2" and "mp3" files can be recovered from an infected system.
Once executed, this virus drops the following files:
\windows\Win32DLL.vbs \system\MSKernel32.vbs \system\LOVE-LETTER-FOR-YOU.TXT.vbs.
\system\LOVE-LETTER-FOR-YOU.HTM
It also modifies the following registry entries so that the virus is executed at each Windows starts up:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\ CurrentVersion\Run\MSKernel32" :\windows\system \MSKernel32.vbs
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices\Win32DLL” :\windows\\Win32DLL.vbs
It searches for a file named WinFAT32.exe in the :\Windows\system folder. If the file does not exist, it modifies Internet Explorer’s startup page with one of the following sites:
http://www.skyinet.net/~young1s/
HJKhjnwerhjkxcvytwertnMTFwetrdsfmhPnjw6587345gvsdf7679njbvYT/
WIN-BUGSFIX.exe
http://www.skyinet.net/~angelcat/skladjflfdjghKJnwetryDGFikjUIy
qwerWe546786324hjk4jnHHGbvbmKLJKjhkqj4w/WIN-BUGSFIX.exe http://www.skyinet.net/~koichi/jf6TRjkcbGRpGqaq198vbFV5hf
FEkbopBdQZnmPOhfgER67b3Vbvg/WIN-BUGSFIX.exe
http://www.skyinet.net/~chu/sdgfhjksdfjklNBmnfgkKLHjkqwtuHJBh
AFSDGjkhYUgqwerasdjhPhjasfdglkNBhbqwebmznxcbvnmadshfgqw
237461234iuy7thjg/WIN-BUGSFIX.exe
It also searches your system for a file called WIN-BUGSFIX.exe (same as WinFAT32.exe). Before searching the file, the virus first checks whether the key Download Directory located at HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\
contains a value. If it does, the virus proceeds to look for the file WIN-BUGSFIX.EXE at the path specified in the Download Directory key. But if the registry key does not contain any value, then the virus looks for WIN-BUGSFIX.EXE at C:\. VBS_LOVELETTER and then modifies Internet Explorer’s startup page to “about:blank”.
It also modifies the registry key to : HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\
CurrentVersion\Run\WIN-BUGSFIX,\WIN-BUGSFIX.exe if Download Directory contains a value, or to HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\
CurrentVersion\Run\WIN-BUGSFIX ,C:\WIN-BUGSFIX.EXE if it does not contain a value.
The file WIN-BUGSFIX.EXE is actually a password stealing Trojan.
How Do I Remove the Virus?
Unfortunately after the virus has struck there's not much that can be done to retrieve the destroyed data except to reload the destroyed files from a backup. However, after updating your anti-virus program or buying one, then follow these steps to correct the registry and get your computer working again.
Using the REGEDIT program, remove the following keys from your Windows registry.
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion \Run\ MSKernel32=C:\WINDOWS\SYSTEM\MSKernel32.vbs
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion \RunServices\ Win32DLL=C:\WINDOWS\Win32DLL.vbs
Not comfortable with Regedit? You can download a small free program called Love_Letter_Clean.exe from Computer Associates, Inc. that automatically removes the registry keys for you. It's available here. When you click on the link, select "Open this file from it's current location" and click OK, or visit any of the top virus protection site like McAfee, Norton, or Trend Micro to download a similar program..
Finally, let's straighten out your IE home page, which the virus reset to www.skyinet.net. From IE's Tools menu, select Internet Options. Right at the top of the dialog you'll see the Home page setting. Type in the URL of the page you use for your home page, and click Ok. That should be it. If you followed all the steps above your system should be free and clean from this painful love letter.
Information on NewLove - a far more dangerous worm/virus
On May 19th a far more dangerous variation of the LoveLetter worm struck, the worm spreads via Microsoft Outlook and sends itself to everyone in the address book just like its predecessor, but this version overwrites ALL files that are not currently in use at the time of the infection. Thus destroying most everything on the hard drive. It also is more dangerous because it changes the wording in the subject line and the name of the attachment it sends by picking a random filename from the users Start folder or making one up.
The ILOVEYOU virus is an email attachment written in Visual Basic and smartly disguised as a love letter. Who wouldn't want to receive a love letter afterall? The email attachment was called LOVE-LETTER-FOR-YOU.TXT.vbs and when opened wrecked havoc throughout a computer system by overwriting files or hiding them throughout the system and in the case of people using Microsoft Outlook it sent a copy of the virus to everyone in the computer's address book.
The Love Bug infects files with the following extensions: "vbs", "vbe", "js", "jse", "css", "wsh", "sct", "hta", "jpg", "jpeg", "mp3", or "mp2". Except for "mp3" and "mp2" files, the virus overwrites the whole file with its virus code and the original file is destroyed.
For "vbs" and "vbe" files the virus does not change the host filename.
For "js", "jse", "css", "wsh", "sct" or "hta" files
It changes the filename to "
For "jpg" and "jpeg" files
It changes the filename to "
For "mp3", or "mp2" files
It changes the attribute of the original audio file as the hidden system file and creates a copy of the virus self in the filename of "
Once executed, this virus drops the following files:
\windows\Win32DLL.vbs \system\MSKernel32.vbs \system\LOVE-LETTER-FOR-YOU.TXT.vbs.
\system\LOVE-LETTER-FOR-YOU.HTM
It also modifies the following registry entries so that the virus is executed at each Windows starts up:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices\Win32DLL” :\windows\\Win32DLL.vbs
It searches for a file named WinFAT32.exe in the :\Windows\system folder. If the file does not exist, it modifies Internet Explorer’s startup page with one of the following sites:
http://www.skyinet.net/~young1s/
HJKhjnwerhjkxcvytwertnMTFwetrdsfmhPnjw6587345gvsdf7679njbvYT/
WIN-BUGSFIX.exe
http://www.skyinet.net/~angelcat/skladjflfdjghKJnwetryDGFikjUIy
qwerWe546786324hjk4jnHHGbvbmKLJKjhkqj4w/WIN-BUGSFIX.exe http://www.skyinet.net/~koichi/jf6TRjkcbGRpGqaq198vbFV5hf
FEkbopBdQZnmPOhfgER67b3Vbvg/WIN-BUGSFIX.exe
http://www.skyinet.net/~chu/sdgfhjksdfjklNBmnfgkKLHjkqwtuHJBh
AFSDGjkhYUgqwerasdjhPhjasfdglkNBhbqwebmznxcbvnmadshfgqw
237461234iuy7thjg/WIN-BUGSFIX.exe
It also searches your system for a file called WIN-BUGSFIX.exe (same as WinFAT32.exe). Before searching the file, the virus first checks whether the key Download Directory located at HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\
contains a value. If it does, the virus proceeds to look for the file WIN-BUGSFIX.EXE at the path specified in the Download Directory key. But if the registry key does not contain any value, then the virus looks for WIN-BUGSFIX.EXE at C:\. VBS_LOVELETTER and then modifies Internet Explorer’s startup page to “about:blank”.
It also modifies the registry key to : HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\
CurrentVersion\Run\WIN-BUGSFIX,
CurrentVersion\Run\WIN-BUGSFIX ,C:\WIN-BUGSFIX.EXE if it does not contain a value.
The file WIN-BUGSFIX.EXE is actually a password stealing Trojan.
How Do I Remove the Virus?
Unfortunately after the virus has struck there's not much that can be done to retrieve the destroyed data except to reload the destroyed files from a backup. However, after updating your anti-virus program or buying one, then follow these steps to correct the registry and get your computer working again.
Using the REGEDIT program, remove the following keys from your Windows registry.
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion \Run\ MSKernel32=C:\WINDOWS\SYSTEM\MSKernel32.vbs
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion \RunServices\ Win32DLL=C:\WINDOWS\Win32DLL.vbs
Not comfortable with Regedit? You can download a small free program called Love_Letter_Clean.exe from Computer Associates, Inc. that automatically removes the registry keys for you. It's available here. When you click on the link, select "Open this file from it's current location" and click OK, or visit any of the top virus protection site like McAfee, Norton, or Trend Micro to download a similar program..
Finally, let's straighten out your IE home page, which the virus reset to www.skyinet.net. From IE's Tools menu, select Internet Options. Right at the top of the dialog you'll see the Home page setting. Type in the URL of the page you use for your home page, and click Ok. That should be it. If you followed all the steps above your system should be free and clean from this painful love letter.
Information on NewLove - a far more dangerous worm/virus
On May 19th a far more dangerous variation of the LoveLetter worm struck, the worm spreads via Microsoft Outlook and sends itself to everyone in the address book just like its predecessor, but this version overwrites ALL files that are not currently in use at the time of the infection. Thus destroying most everything on the hard drive. It also is more dangerous because it changes the wording in the subject line and the name of the attachment it sends by picking a random filename from the users Start folder or making one up.
How to remove porn sites interrupting in your home computer
Many people may enconter these problem while browsing on your home computer .
i.e,, porn sites coming in to the picture. some sites ,unknown tool bars in the internet explorers,
unwanted interrupting messages such as your computer contains large porn matter.download this software to remove these with some porn matter. use the related link given belowThese can distrub you so much .
there is way to remove these.
use this link it is very use ful . It is free and very very useful
down load the file and first scan with it
and then in safemode heal the infected files and the rgistry any thing else in your computer.
follow the instructions from the site and do as in the procedure given in the webpage
how to change the name of recyclebin?
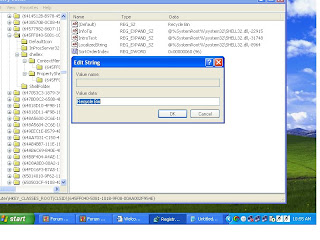
how to change the name of recyclebin?
by editing the registry we can change the name .
process:-
1) goto start-> Run ->type regedit
2)in the registry editor
gofor the key HKEY-CLASSES_ROOT->CLSID->645FF040-5081-101B-90F8-00AA002F954E
in this folder we cn get recyclebin to this key in right hand side make a right cklick and in value data type your name what you wanton recyclebin
by editing the registry we can change the name .
process:-
1) goto start-> Run ->type regedit
2)in the registry editor
gofor the key HKEY-CLASSES_ROOT->CLSID->645FF040-5081-101B-90F8-00AA002F954E
in this folder we cn get recyclebin to this key in right hand side make a right cklick and in value data type your name what you wanton recyclebin
How to Remove Individual Entries from Run Command History
What is the Run Command History?
Many items in Windows use a MRU (Most Recently Used) List to keep lists of filenames, commands, etc. The Run command in the Start Menu keeps a list of the last several commands you entered. If you are like me, you use the run command quite frequently to open the Windows Registry, run a particular program like Notepad, or open a utility like the calculator. However, there are many times that I would like to delete one entry in this list but leave the others. Utilties such as Window Washer or CCleaner have options to clear this Run MRU list each time they are activated, however I want to selectively delete items in the list and keep my most used items handy for later.
The RUNMRU list is stored in the Windows Registry in the following location:HKEY_CURRENT_USER\ Software\ Microsoft\ Windows\ CurrentVersion\ Explorer\ RunMRU\It includes each command that you most recently used along with a key called MRUList that keeps the order the commands should appear in the list. See the screenshot below:
By opening the Registry Editor you can go to the registry key and right-click on the command you wish to remove and delete it. Close the Registry Editor and restart your computer and the list will be changed.
By opening the Registry Editor you can go to the registry key and right-click on the command you wish to remove and delete it. Close the Registry Editor and restart your computer and the list will be changed.
Is There a Program to Delete Individual Entries from the RUNMRU List?
Many of my customers would rather not edit the Windows registry to remove these individual entries, so I setup a VBScript that you can download and run to delete individual commands from this list. Follow these instructions to download and use this program to clear unwanted entries from the Run Command history.
1) Click on the following link and download the EditRunMRUList.vbs script to your desktopDownload EditRunMRUList.vbs
2) Double-click on the editrunmrulist.vbs file
3) The program will open and tell you how many entries are cur rently in the RUNMRU list, then it will ask you if you want to edit the list now, click Yes to continue.
rently in the RUNMRU list, then it will ask you if you want to edit the list now, click Yes to continue.
 rently in the RUNMRU list, then it will ask you if you want to edit the list now, click Yes to continue.
rently in the RUNMRU list, then it will ask you if you want to edit the list now, click Yes to continue.4) The next screen will show you the first command in the list and ask you if you want to delete it. Click on Yes to Delete or No to Keep it.The program will proceed through each command in the list allowing you to keep or delete the command.

5) After cycling through each command, the program will remind you to Restart Your Computer before the change will take effect.
Windows errors related to svchost.exe ?
svchost.exe is a system process belonging to the Microsoft Windows Operating System which handles processes executed from DLLs.
2)This program is important for the stable and secure running of your computer and should not be terminated.
3) svchost.exe is a process registered as a backdoor vulnerability which may be installed for malicious purposes by an attacker allowing access to your computer from remote locations, stealing passwords, Internet banking and personal data.
4)It is a process which is registered as a trojan. This Trojan allows attackers to access your computer from remote locations, stealing passwords, Internet banking and personal data. This process is a security risk and should be removed from your system.
5)It is a process belonging to Microsoft Service Host Process. This could also be a stealth monitoring software that sits in the background and tracks all activities such as keyboard input (including websites visited, passwords etc.) This information can be sent to third parties through email or ftp uploads. If you did not intentionally install this program make sure you remove it to protect your privacy.Determining whether svchost.exe is a virus or a legitimate Windows process depends on the directory location it executes or runs from
2)This program is important for the stable and secure running of your computer and should not be terminated.
3) svchost.exe is a process registered as a backdoor vulnerability which may be installed for malicious purposes by an attacker allowing access to your computer from remote locations, stealing passwords, Internet banking and personal data.
4)It is a process which is registered as a trojan. This Trojan allows attackers to access your computer from remote locations, stealing passwords, Internet banking and personal data. This process is a security risk and should be removed from your system.
5)It is a process belonging to Microsoft Service Host Process. This could also be a stealth monitoring software that sits in the background and tracks all activities such as keyboard input (including websites visited, passwords etc.) This information can be sent to third parties through email or ftp uploads. If you did not intentionally install this program make sure you remove it to protect your privacy.Determining whether svchost.exe is a virus or a legitimate Windows process depends on the directory location it executes or runs from
How to Speed Up Windows Boot Time ?




How to speed up the time it takes Windows to load or boot.
There are a variety of factors (both hardware and software) involved in lowering the amount of time it takes for Windows to load. I will go over most of these ways in this page starting with changes in the system BIOS and moving onward from there.
All of these changes are optional, and do not need to be carried out. Instead, they are offered as suggestions to try to lower the time it takes for Windows to boot. Some of these changes are very advanced and should only be attempted if you are comfortable with making the changes and have your data backed up.
System BIOS Changes One of the first places to help speed boot time in Windows is to make some simple changes to the system BIOS. The BIOS or Basic Input/Output System is a set of instructions and commands built into the motherboard that allows the computer to know what type of hardware is connected and how to communicate with that hardware. You'll first have to gain access to the BIOS setup screen to make any changes.
Do not make changes to the system settings in the BIOS lightly, one mistake can render the computer unbootable and cause more problems than its worth. For this reason, do not attempt making changes to the system BIOS unless you are willing to accept the risk along with it.
With that said, you'll want to follow the directions below and make some simple changes to speed up the boot process.
1) You must start with the computer completely off, not in sleep or hibernation mode. Then turn the computer on.
2) Enter the system BIOS screen by the manufacturers suggestion. Depending on the computer, this may involve pressing the DEL key, pressing F1, Pressing F10, holding down CTRL-ALT-S, or a variety of other keystrokes to get to the BIOS screen. For a more complete list of keystrokes to enter the BIOS screen, visit Michael Steven's page on the subject.
3) Once in the BIOS setup, look for a BOOT menu and select it with your keyboard arrow keys, Tab, and Enter.4) In most modern BIOS screens, you'll find an option for Quick Boot. Enable this to skip memory tests and other minor Power On Self Tests
5) Find an option for Boot Device Priority next, and change the first boot device to be the hard drive. Changing this option will speed up the boot process, but it will also not allow the computer to boot from a floppy disk or CD-ROM. If booting from anything other than the hard drive is important to you, please skip this step. If later on, you need to boot from a CD-ROM, simply re-enter the BIOS setup and make the CD-ROM the first boot device.
6) Choose the option to Exit and Save Changes and the computer will reboot.There are other options in the BIOS to speed up boot time such as choosing the exact settings for your hard drive, and disabling AUTO DETECT of hard drives and other media. However I am skipping those changes and leaving them for a later discussion. Changes to Windows SettingsThe next group of changes to consider will be to the many Windows settings.
We will use a handy tool called the System Configuration Utility to accomplish most of these changes. Follow the steps below to open and use this tool.
Startup Tab Changes
1) Click on Start, Run and type MSCONFIG and press Enter
2) Click on the STARTUP tab in the System Configuration Utility to view all the items that begin on Startup. An example is shown below.Each item on the Startup tab that is checked loads immediately after Windows starts. If there are lots of items here, this will slow down the boot time for Windows considerably. Each of these items can be toggled on or off simply by using the checkmark box to the left of the item. The column directly to right of the checkmark is the Name of the program, while the next column over is the location on the hard drive or other device of the file. Finally the last column shows where in the computer the file is started from. This location could be in the registry as is the case with all the locations that begin with HKLM or HKCU, or it could be in the Windows Startup folder found under ALL PROGRAMS in Windows XP.You can examine each of these startup items and uncheck any that are not necessary. How do you know which ones are not necessary? Well, in most computer configurations, you'll want drivers running for your graphics or video controller and sound card, and most likely an antivirus and firewall running. Other startup items are usually extras that could be eliminated from boot up. To discover what a particular item is used for, jot down the name for the item and go over to a site called Process Library, type in the name of the process and click Find. This is a very handy tool for discovering which startup items are truly needed.When you are done modifying the checkmarks to the Startup tab, click OK and you'll be asked to reboot the system.
Windows Services ChangesOnce the computer is rebooted, click on Start, Run and type MSCONFIG and press Enter again. This will reopen the System Configuration Utility. Click on the Services tab, then click on the option at the bottom called "Hide All Microsoft Services" to see what unnecessary Windows services are running that can be removed. Generally speaking, you want services related to your video/sound cards and antivirus or firewall programs left running. Other services may not be essential and can be removed. Remember to only remove unessential services or you risk experiencing boot problems.
Use Google to search for information on unfamiliar services. Another good resource is Black Viper's Strange Services page.Hardware Changes to Increase Boot TimeAdding more Memory (RAM)Other than upgrading the motherboard and CPU, you can generally increase the amount of RAM in your computer to make it load programs and applications faster and provide a more enjoyable computing experience.
You'll want to check your motherboard to make sure you have available slots and the maximum amount of RAM you can add to your particular motherboard.Replacing your Hard Drive with a Faster RPM DriveIf you have a slower hard drive such as a 5400 RPM or slower, you may want to consider upgrading to a faster 7200 RPMhard drive. The difference in RPM speed will generally be quite noticeable.
Use Google to search for information on unfamiliar services. Another good resource is Black Viper's Strange Services page.Hardware Changes to Increase Boot TimeAdding more Memory (RAM)Other than upgrading the motherboard and CPU, you can generally increase the amount of RAM in your computer to make it load programs and applications faster and provide a more enjoyable computing experience.
You'll want to check your motherboard to make sure you have available slots and the maximum amount of RAM you can add to your particular motherboard.Replacing your Hard Drive with a Faster RPM DriveIf you have a slower hard drive such as a 5400 RPM or slower, you may want to consider upgrading to a faster 7200 RPMhard drive. The difference in RPM speed will generally be quite noticeable.
Changing to Static IPIf your computer is connected to a local area network that you control and you have a DHCP server enabled on your router, during the boot process the computer queries the network to valid IP address. You can shave seconds off your boot time by assigning a valid IP address to your computer instead of using DHCP to assign it.
To setup a Static IP for your computer
follow these directions.
1) Click on Start, Run
2) Type NCPA.CPL and press Enter to open the Network Connection Control Panel
3) Right-click on the Local Area Connection and choose Properties
4) Click on Internet Protocol (TCP/IP) and click Properties
5) You should see a screen similar to the one below. Fill in your static IP, subnet, default gateway, and DNS server information and click OK.
If you aren't sure of your IP ranges on your router, consult your router manual or a friend that is more knowledgeable in networking terminology. Again, this is an optional item and does not necessarily need to be accomplished. Using DHCP is fine, although you sacrifice a few seconds for an IP to be assigned to from the network.Switching from Master/Slave to Cable SelectIn a recent article, I talk about how changing the configuration on the hard drive from Master to Cable Select reduced the boot time on this particular machine by 2 minutes.
Other Windows Performance Tips
Reduce the Number of Fonts installedEvery font that is installed in Windows has to load when Windows starts. The more fonts you have installed, the slower Windows loads. Although you can safely have around 1000 fonts loaded in Windows, I like to keep my font list closer to 300-500 or fewer if possible. There are certain fonts that are definitely required by Windows, so be careful in removing any fonts from your computer unless you know they are not needed. Fonts such as Verdana,Arial,Trebuchet, Tahoma, Tahoma, Times New Roman, MS Sans Serif, and Courier New should be left on your system.
Reduce the Number of Fonts installedEvery font that is installed in Windows has to load when Windows starts. The more fonts you have installed, the slower Windows loads. Although you can safely have around 1000 fonts loaded in Windows, I like to keep my font list closer to 300-500 or fewer if possible. There are certain fonts that are definitely required by Windows, so be careful in removing any fonts from your computer unless you know they are not needed. Fonts such as Verdana,Arial,Trebuchet, Tahoma, Tahoma, Times New Roman, MS Sans Serif, and Courier New should be left on your system.
Follow the directions below to remove extra fonts from Windows XP.
1) Open My Computer
2) Double-click on Drive C
3) Click on File, New Folder and title it Fonts Backup
4) Double-click on the Windows folder to open it
5) Double-click on the Fonts folder
6) Highlight the fonts you wish to remove, click on Edit and choose COPY
7) Navigate back to the C:\Fonts Backup folder and PASTE these fonts into your backup folder
8) Return to the Fonts Folder and right-click on any fonts you previously copied to the backup folder, then choose Delete.
If you accidentally removed a font, simply reverse the procedure by copying and pasting the font back into the Windows\Fonts folder.
Disk Cleanup, Scandisk, and DefragPerforming regular hard drive maintenance on your computer every few months will not only catch problems before they cause serious damage but also make your hard drive run at its optimal level. Follow these instructions to clean up the drive and defrag it.
1) Open My Computer
2) Right-click on the hard drive usually Drive C
3) Click on the Tools tab
4) Under Error Checking, click on Check Now. Optionally, you may want to check the boxes to "Automatically Fix File Errors" and "Scan For and Attempt Recovery for Bad Sectors"
5) Next, click on the General tab and click on Disk Cleanup.
After the computer calculates the amount of files to remove, place a checkmark next to the type of files you wish to remove and click Ok. Read the descriptions for each type of file to determine if you should delete it.
6) Finally, click on the Tools tab again and under Defragmentation click Defragment Now
7) Click on the hard drive you wish to defrag, click on Analyze and then click on Defragment. This process may take some time to complete.Virus/Spyware ScansFinally, you'll want to complete a thorough virus and spyware scan of your system.
I recommend running an online virus scan first, then a check for spyware. You can click on the following links to check your system for viruses.
when does Orkut is banned appears?
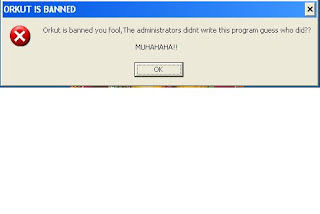
When we open the site www.orkut.com the message Orkut is banned...you fool!! appears
is caused due to a virus Heap41a.
This is removed by using Task manager ( CTRL+ALT+DEl)press the tab processes if in that a process named svchost.exe is running with the user name , then remove it by doing end task
if the site is blocked :goto www.hidemyass.com and type the url (www.orkut.com) there and it ll open.
2. Click start->run->regedit
3. press ctrl + f and type "heap32a"
4. delete all values by this name.
5. close regedit and open "My Computer"
6. in the address bar type "c:\Heap32a"
7. press ctrl + A and shift + del all the items.
Fixing Disabled Task Manager

Task Manager Has Been Disabled, How to Fix It?
Many times when working on a computer that has been infected with a virus, trojan, or piece of spyware I find myself with the Task Manager being disabled. Malware creators like to disable Task Manager so it makes solving the problem and removing the issue difficult.If this happens you'll normally have to edit the Windows registry to fix the problem. A restriction has been placed on the user to not allow them to run Task Manager, this might be ok in an office environment where the IT department wants to control things, but in a home office this can cause major problems trying to fix a malware or virus issue.Listed below you will find the many ways to reenable Task Manager along with an automatic method that works wonders. First we'll begin with the various registry modification methods for correcting this problem.
Method 1 - Using the Group Policy Editor in Windows XP ProfessionalClick Start, Run, type gpedit.msc and click OK. Under User Configuration, Click on the plus (+) next to Administrative Templates Click on the plus (+) next tSystem, then click on Ctrl+Alt+Delete Options Find Remove Task Manager in the right-hand pane and double click on it Choose the option "Not Configured" and click Ok. Close the Group Policy Window
Method 2: Change the Task Manager Option through the Run lineClick on Start, Run and type the following command exactly and press Enter REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 0 /f
Method 3: Change Task Manager through a Registry REG fileClick on Start, Run, and type Notepad and press Enter Copy and paste the information between the dotted lines into Notepad and save it to your desktop as taskmanager.reg ------------------------------------Windows Registry Editor Version 5.00[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System]"DisableTaskMgr"=dword:00000000-------------------------------------3. Double click on the taskmanager.reg file to enter the information into the Windows registry
Method 4: Delete the restriction in the registry manuallyClick on Start, Run, and type REGEDIT and press Enter Navigate to the following branchHKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies\ SystemIn the right pane, find and delete the value named DisableTaskMgr Close the registry editor
Method 5: Download and Run FixTaskManager program Click on the following links and download the program FixTaskManager to your DesktopMain SiteBackup LocationDouble-click on the file FixTaskManager on your desktop and run it
error deleting file or folder

Many times when trying to remove an unwanted program, especially a piece of adware or spyware, you may run across a file that is undeletable by any normal method. When you try to remove it you'll receive the error message shown below telling you "access denied" and explaining the file may be in use. You may also receive one of the following messages.Cannot delete file: Access is deniedThere has been a sharing violation.The source or destination file may be in use.The file is in use by another program or user.Make sure the disk is not full or write-protected and that the file is not currently in use.So if the file is in use, how do you delete it?I'll show you several ways of removing these types of files and even some freeware programs that help you remove these pesky undeletable files.
Windows 95/98/ME
If you are using Windows 95, 98, or Windows ME, the easiest way to remove an undeleteable file is to boot to a DOS prompt and manually delete the file. Before you do this, you'll want to make a note of the location of the file including the entire path to it. Follow the steps below to delete these types of files.If you already know the path to the file, please skip to Step 7
1)Click on Start, Find, Files and Folders
2)Type the name of the undeletable file in the Named or Search For box
3)Make sure the Look In box shows the correct drive letter
4)Click on Find Now or Search Now and let the computer find the file
5)Once the file is located, right-click on it and choose properties, make a note of the file location. Usually this is something similar to c:\windows\system32\undeleteablefilesname.exe
Close the search box
6)Locate a boot disk for your version of Windows, if you do not have a boot disk, follow the steps on the link below to create an emergency boot disk.How to Create an Emergency Boot Disk for Windows
7)Shut down and restart your computer with the boot disk in your floppy drive.
The computer will boot to a DOS prompt that will look similar to c:\
Type the following command and press Enter to delete the filer, substituting the phrase
Remove the boot disk in the floppy drive and restart your computer
The file should now be deleted.
Windows XP
In Windows XP, there are a couple ways to remove an undeleteable file, a manual way, and a couple automated ways using some freeware programs. First, I'll show you the manual way.Manual MethodIf you already know the path to the file, please skip to Step 7
Click on Start, Search, All Files and Folders
Type the name of the undeletable file in the box shown
Make sure the Look In box shows the correct drive letter
Click Search and let the computer find the file
Once the file is located, right-click on it and choose properties, make a note of the file location. Usually this is something similar to c:\windows\system32\undeleteablefilesname.exe
Close the search box
Click on Start, Run, and type CMD and Press Enter to open a Command Prompt window
Leave the Command Prompt window open, but proceed to close all other open programs
Click on Start, Run and type TASKMGR.EXE and press Enter to start Task Manager
Click on the Processes tab, click on the process named Explorer.exe and click on End Process.
Minimize Task Manager but leave it open
Go back to the Command Prompt window and change to the directory where the file is located. To do this, use the CD command. You can follow the example below.Example: to change to the Windows\System32 directory you would enter the following command and Press Entercd \windows\system32
Now use the DEL command to delete the offending file.
Type DEL where is the file you wish to delete.Example: del undeletable.exe
Use ALT-TAB to go back to Task Manager
In Task Manager, click File, New Task and enter EXPLORER.EXE to restart the Windows shell.
Close Task ManagerPrograms to automatically delete a fileRemove on Reboot Shell Extension
This is a nice extension that loads into the right click menu. All you have to do is right-click on a file and choose "Remove on Next Reboot" and the file will be deleted the next time the computer restarts. Although it probably should only be used by more advanced computer users since it may be TOO easy to delete files using this program. Pocket Killbox
A simple .exe file that you can use to delete undeleteable files, although the program will also delete temporary files, edit the HOSTS file, and more. A definite must have program when you are fighting an annoying spyware or adware program that won't remove. Unlocker
Unlocker is another program that runs from the right click menu. Its simple and very effective. The website even has a side by side comparision of other programs that accomplish this task.
Using one of the three tools shown above, you should be able to remove those annoying undeleteable files once and for all.
Use ALT-TAB to go back to Task Manager
In Task Manager, click File, New Task and enter EXPLORER.EXE to restart the Windows shell.
Close Task ManagerPrograms to automatically delete a fileRemove on Reboot Shell Extension
This is a nice extension that loads into the right click menu. All you have to do is right-click on a file and choose "Remove on Next Reboot" and the file will be deleted the next time the computer restarts. Although it probably should only be used by more advanced computer users since it may be TOO easy to delete files using this program. Pocket Killbox
A simple .exe file that you can use to delete undeleteable files, although the program will also delete temporary files, edit the HOSTS file, and more. A definite must have program when you are fighting an annoying spyware or adware program that won't remove. Unlocker
Unlocker is another program that runs from the right click menu. Its simple and very effective. The website even has a side by side comparision of other programs that accomplish this task.
Using one of the three tools shown above, you should be able to remove those annoying undeleteable files once and for all.
Unexpectedly slow startup in Windows 7 or in Windows Server 2008 R2
Consider the following scenario:
In this scenario, the computer has an unexpectedly slow startup time after a change is made to the default DPI display setting. Then, the computer has an unexpectedly slow startup time every other time that the computer is started.
o determine whether you must apply this hotfix, verify the setting of the Make text or other items larger or smaller option on your computer. To do this, follow these steps:
If the setting is set to a different value, you may have to apply this hotfix.
If this hotfix does not resolve the problem on your computer, try to optimize Windows 7 for better performance. To do this, visit the following Microsoft Web site:
If the hotfix is available for download, there is a "Hotfix download available" section at the top of this Knowledge Base article. If this section does not appear, contact Microsoft Customer Service and Support to obtain the hotfix.
Note If additional issues occur or if any troubleshooting is required, you might have to create a separate service request. The usual support costs will apply to additional support questions and issues that do not qualify for this specific hotfix. For a complete list of Microsoft Customer Service and Support telephone numbers or to create a separate service request, visit the following Microsoft Web site:
- You have a computer that is running Windows 7 or Windows Server 2008 R2.
- This computer is connected to a high resolution monitor.
- On this computer, the default dots per inch (DPI) display setting is set to a value other than 96 DPI.
In this scenario, the computer has an unexpectedly slow startup time after a change is made to the default DPI display setting. Then, the computer has an unexpectedly slow startup time every other time that the computer is started.
o determine whether you must apply this hotfix, verify the setting of the Make text or other items larger or smaller option on your computer. To do this, follow these steps:
- Click Start, and then click Control Panel.
- Click Hardware and Sound.
- Click Make text or other items larger or smaller.
If the setting is set to a different value, you may have to apply this hotfix.
If this hotfix does not resolve the problem on your computer, try to optimize Windows 7 for better performance. To do this, visit the following Microsoft Web site:
http://windows.microsoft.com/en-us/windows7/Optimize-Windows-7-for-better-performance (http://windows.microsoft.com/en-us/windows7/Optimize-Windows-7-for-better-performance)
Hotfix information
A supported hotfix is available from Microsoft. However, this hotfix is intended to correct only the problem that is described in this article. Apply this hotfix only to systems that are experiencing the problem described in this article. This hotfix might receive additional testing. Therefore, if you are not severely affected by this problem, we recommend that you wait for the next software update that contains this hotfix.If the hotfix is available for download, there is a "Hotfix download available" section at the top of this Knowledge Base article. If this section does not appear, contact Microsoft Customer Service and Support to obtain the hotfix.
Note If additional issues occur or if any troubleshooting is required, you might have to create a separate service request. The usual support costs will apply to additional support questions and issues that do not qualify for this specific hotfix. For a complete list of Microsoft Customer Service and Support telephone numbers or to create a separate service request, visit the following Microsoft Web site:
http://support.microsoft.com/contactus/?ws=support (http://support.microsoft.com/contactus/?ws=support)
Note The "Hotfix download available" form displays the languages for which the hotfix is available. If you do not see your language, it is because a hotfix is not available for that language.Prerequisites
To apply this hotfix, you must have one of the following Windows operating systems installed:- Windows 7
- Windows Server 2008 R2
Restart information
You must restart the computer after you apply this hotfix.File information
The English version of this hotfix has the file attributes (or later file attributes) that are listed in the following table. The dates and times for these files are listed in Coordinated Universal Time (UTC). When you view the file information, it is converted to local time. To find the difference between UTC and local time, use the Time Zone tab in the Date and Time item in Control Panel.For all supported x86-based versions of Windows 7
Collapse this tableExpand this table
| File name | File version | File size | Date | Time | Platform |
|---|---|---|---|---|---|
| Win32k.sys | 6.1.7600.16484 | 2,326,528 | 11-Dec-2009 | 03:57 | x86 |
| Win32k.sys | 6.1.7600.20594 | 2,326,528 | 11-Dec-2009 | 03:57 | x86 |
For all supported x64-based versions of Windows Server 2008 R2
Collapse this tableExpand this table
| File name | File version | File size | Date | Time | Platform |
|---|---|---|---|---|---|
| Win32k.sys | 6.1.7600.16484 | 3,122,176 | 11-Dec-2009 | 05:52 | x64 |
| Win32k.sys | 6.1.7600.20594 | 3,122,176 | 11-Dec-2009 | 05:55 | x64 |
For all supported Itanium-based versions of Windows Server 2008 R2
Collapse this tableExpand this table
| File name | File version | File size | Date | Time | Platform |
|---|---|---|---|---|---|
| Win32k.sys | 6.1.7600.16484 | 7,411,712 | 11-Dec-2009 | 03:50 | IA-64 |
| Win32k.sys | 6.1.7600.20594 | 7,411,712 | 11-Dec-2009 | 03:47 | IA-64 |
How to Find Your Own IP Address
How to Find Your Own IP Address
By default, Windows Vista is not set to show the Run command from the Start menu. You can change this in Vista Preferences or use Search to find the Run command.
To use the Search command in Windows Vista type:
From the _>Start menu ----> Search
Type Run Double-click the Run shortcut
From the Start menu ----> Run Type cmd in the Run
Type ipconfig /all
Using the Web
Use this webpage, provided by Networking and Telecommunications Services (NTS), to give you your hostname and IP address: https://nts-service.umd.edu/
By default, Windows Vista is not set to show the Run command from the Start menu. You can change this in Vista Preferences or use Search to find the Run command.
To use the Search command in Windows Vista type:
From the _>Start menu ----> Search
Type Run Double-click the Run shortcut
From the Start menu ----> Run Type cmd in the Run
Type ipconfig /all
Using the Web
Use this webpage, provided by Networking and Telecommunications Services (NTS), to give you your hostname and IP address: https://nts-service.umd.edu/
Torjan mal ware Win32:MalOb-Z [Cryp]
this mainly gets problems with AVAST Users .Boot time scan gets disabled and asks for boot scan for every restart but it gets detects in scan of memory but it cannot be deleted and shows the message " this cannot be deleted as it is used by another process and virus alerts for every 30-40 secs.
Solution
this can solve 90%%%%
Before engaging into the scanning and/or cleaning process. Please clean all Temporary Files by using either of these tools: Windows Disk Cleanup or CCleaner.
===== Malwarebytes' Antimalware (MBAM) =====
(1) Download Malwarebyes' Antimalware here.
(2) After downloading, proceed to installation.
(3) On the last dialog box, do not forget to leave Update Malwarebytes' Antimalware checked.
(4) Malwabytes' Antimalware GUI would appear, from there select Perform Quick Scan and click Scan
Solution
this can solve 90%%%%
Before engaging into the scanning and/or cleaning process. Please clean all Temporary Files by using either of these tools: Windows Disk Cleanup or CCleaner.
- Disk Cleanup:
Press Windows Key + R
Type in: cleanmgr
Put a check beside: Temporary Internet Files | Temporary Files | Old Chkdsk Files
Click OK - CCLeaner
Download CCleaner here
Install CCleaner & double click the desktop icon
CCleaner GUI will appear, click on Analyze & wait for scanning to complete
Click on Run Cleaner
===== Malwarebytes' Antimalware (MBAM) =====
(1) Download Malwarebyes' Antimalware here.
(2) After downloading, proceed to installation.
(3) On the last dialog box, do not forget to leave Update Malwarebytes' Antimalware checked.
(4) Malwabytes' Antimalware GUI would appear, from there select Perform Quick Scan and click Scan
A Program Stops Responding or CPU Usage Approaches 100 Percent When You Unplug a USB Microphone in Windows 2000 or Windows XP
When you unplug a Universal Serial Bus (USB) microphone, you may experience any of the following symptoms:
Microsoft has confirmed that this problem occurs in Windows 2000 if you unplug a microphone that uses the Microsoft Usbaudio.sys driver while the microphone is being used by a program. This problem may also occur in Windows XP.
To work around this problem, do not unplug a USB microphone when audio is being played back. You might also be able to work around this problem by installing the End-User Runtime package.
The following file is available for download from the Microsoft Download Center:
 Download the DirectX 9.0a End-User Runtime package now. (http://www.microsoft.com/downloads/details.aspx?familyid=886ACB56-C91A-4A8E-8BB8-9F20F1244A8E&displaylang=en) For additional information about how to download Microsoft Support files, click the following article number to view the article in the Microsoft Knowledge Base:
Download the DirectX 9.0a End-User Runtime package now. (http://www.microsoft.com/downloads/details.aspx?familyid=886ACB56-C91A-4A8E-8BB8-9F20F1244A8E&displaylang=en) For additional information about how to download Microsoft Support files, click the following article number to view the article in the Microsoft Knowledge Base:
- A program that is currently using the microphone (such as Microsoft NetMeeting, GraphEdit from the Microsoft DirectShow SDK, or AmCap from the DirectShow SDK) may stop responding.
- Your computer's CPU usage may approach 100 percent.
Microsoft has confirmed that this problem occurs in Windows 2000 if you unplug a microphone that uses the Microsoft Usbaudio.sys driver while the microphone is being used by a program. This problem may also occur in Windows XP.
To work around this problem, do not unplug a USB microphone when audio is being played back. You might also be able to work around this problem by installing the End-User Runtime package.
The following file is available for download from the Microsoft Download Center:
Collapse this imageExpand this image

119591 (http://support.microsoft.com/kb/119591/EN-US/ ) How to Obtain Microsoft Support Files from Online Services
Microsoft scanned this file for viruses. Microsoft used the most current virus-detection software that was available on the date that the file was posted. The file is stored on security-enhanced servers that help to prevent any unauthorized changes to the file.
Csrss.exe uses 100% of the CPU When you Right-Click an item in Explorer
Csrss.exe uses 100% of the CPU When you Right-Click an item in Windows Explorer or on the desktop
Before continuing, make sure you have backed up the contents of your My Documents folder, and any other important data stored in your profile such as application settings. Once your profile is deleted, you will not be able to recover data stored inside of it.
In order to delete your profile, you must be logged in with an account which has administrative privileges which is also not yours. Once you are logged in, open the user profiles list. To locate the list of local user profiles, right-click My Computer, click Properties, and then on the Advanced tab, click Settings under User Profile. Select your profile from the list, and then click Delete.
Logoff, and then log back on as yourself. A new profile will be created when you log on.
CAUTION
If the corrupted profile is that of a domain administrator, and it is located on the first domain controller in the forest, the EFS recovery key must first be backed up. See KB Article 324897 for details on this procedure.
Before continuing, make sure you have backed up the contents of your My Documents folder, and any other important data stored in your profile such as application settings. Once your profile is deleted, you will not be able to recover data stored inside of it.
In order to delete your profile, you must be logged in with an account which has administrative privileges which is also not yours. Once you are logged in, open the user profiles list. To locate the list of local user profiles, right-click My Computer, click Properties, and then on the Advanced tab, click Settings under User Profile. Select your profile from the list, and then click Delete.
Logoff, and then log back on as yourself. A new profile will be created when you log on.
CAUTION
If the corrupted profile is that of a domain administrator, and it is located on the first domain controller in the forest, the EFS recovery key must first be backed up. See KB Article 324897 for details on this procedure.
How to fix CPU 100 % usage
When you run programs, CPU utilization reaches 100 percent. When CPU utilization reaches 100 percent, programs either run slowly or stop responding (hang).
Note To view CPU utilization, press CTRL+ALT+DEL, click Task Manager, and then click the Performance tab.
On multiprocessor computers, you may experience many context switches each second or many system calls each second.
These symptoms occur after you install Microsoft Windows XP Service Pack 2 (SP2).
cause
This problem occurs because of the user interface code that is included in Windows XP SP2. The high CPU utilization is caused by the additional overhead that occurs when the IsWindow function is called by the user interface code
If the hotfix is available for download, there is a "Hotfix download available" section at the top of this Knowledge Base article. If this section does not appear, contact Microsoft Customer Service and Support to obtain the hotfix.
Note If additional issues occur or if any troubleshooting is required, you might have to create a separate service request. The usual support costs will apply to additional support questions and issues that do not qualify for this specific hotfix. For a complete list of Microsoft Customer Service and Support telephone numbers or to create a separate service request, visit the following Microsoft Web site:
Note To view CPU utilization, press CTRL+ALT+DEL, click Task Manager, and then click the Performance tab.
On multiprocessor computers, you may experience many context switches each second or many system calls each second.
These symptoms occur after you install Microsoft Windows XP Service Pack 2 (SP2).
cause
This problem occurs because of the user interface code that is included in Windows XP SP2. The high CPU utilization is caused by the additional overhead that occurs when the IsWindow function is called by the user interface code
Hotfix information
A supported hotfix is available from Microsoft. However, this hotfix is intended to correct only the problem that is described in this article. Apply this hotfix only to systems that are experiencing this specific problem. This hotfix might receive additional testing. Therefore, if you are not severely affected by this problem, we recommend that you wait for the next software update that contains this hotfix.If the hotfix is available for download, there is a "Hotfix download available" section at the top of this Knowledge Base article. If this section does not appear, contact Microsoft Customer Service and Support to obtain the hotfix.
Note If additional issues occur or if any troubleshooting is required, you might have to create a separate service request. The usual support costs will apply to additional support questions and issues that do not qualify for this specific hotfix. For a complete list of Microsoft Customer Service and Support telephone numbers or to create a separate service request, visit the following Microsoft Web site:
http://support.microsoft.com/contactus/?ws=support (http://support.microsoft.com/contactus/?ws=support)
Note The "Hotfix download available" form displays the languages for which the hotfix is available. If you do not see your language, it is because a hotfix is not available for that language.Prerequisites
To apply this hotfix, you must have Windows XP SP2 installed.Restart requirement
You must restart the computer after you apply this hotfix.Hotfix replacement information
This hotfix does not replace any other hotfixes.File information
The English version of this hotfix has the file attributes (or later file attributes) that are listed in the following table. The dates and times for these files are listed in Coordinated Universal Time (UTC). When you view the file information, it is converted to local time. To find the difference between UTC and local time, use the Time Zone tab in the Date and Time item in Control Panel.Date Time Version Size File name -------------------------------------------------------------- 30-Mar-2005 19:53 5.1.2600.2643 577,024 User32.dll 30-Mar-2005 01:30 5.1.2600.2643 1,836,544 Win32k.sys
Subscribe to:
Posts (Atom)
 d
d











